
Copyright infringement not intended
Context:
- After threats by the al-Qaida, comments against Prophet Muhammad — by now-suspended BJP spokesperson Nupur Sharma — have led to a slew of cyber-attacks on Indian websites, both government and private.
- Orchestrated by the hacktivist group DragonForce Malaysia, the series of attacks targeted the Indian embassy in Israel, National Institute of Agriculture Extension Management, and e-portal of the Indian Council of Agriculture Research, among other online platforms.
Cyber Security Imperative For India:
- The ubiquity of smartphones, popularity of social media and thriving digital inclusion projects have been key drivers in the success story of India’s digital economy thus far. However, risks associated with minimal digital literacy or low thresholds of educational attainment and awareness can create significant risks of cyber crime and data misuse.
- Cyber attacks continue to pose risks to critical infrastructure as can be seen with the July 2018 incident In the U.S., when hackers gained access to the control rooms of utility companies, as well as the September 2019 drone attacks on the Saudi Aramco refineries. The vulnerability of critical technological infrastructure is a growing national security concern.
- Since the 2013 National Cyber Security Policy (NCSP), there have been major paradigm shifts that include the push for digital financial inclusion, next generation technological shifts such as Artificial Intelligence, IoT and the Smart Cities Mission. In 2015, Prime Minister Narendra Modi outlined the risks that the world faces from a ‘bloodless’ cyberwar threat. The criticality of ICT and allied areas such as cyber security that operate horizontally is increasing with threats that can be propagated by cyber terrorism, military espionage, corporate espionage and financial frauds. The Hon’ble Prime Minister observed that, given that India is a major service provider in global technology services, solutions around the global problem should emerge from India, not only to enhance cyber security in the country but also to make India a global leader in this realm.
- The World Economic Forum (WEF) Global Risks Report 2019 notes that malicious cyber-attacks and lax cyber security protocols led to massive breaches of personal information in 2018 -- ranging from a security incident at Facebook affecting 50 million users’ data to a personal data breach affecting 150 million users of the MyFitness Pal application.
- In February 2019, India’s Ministry of Electronics and IT (MeitY) outlined India’s digital vision of unlocking the potential of a $1 trillion digital economy by 2025 from its current value of around $200 billion. To realize this potential and build a stable digital economy, it is imperative that all government and private digital systems are safe, secure and resilient.
- As India prepares to refresh its National Cyber Security Policy, it must move in sync with present day technological and ecosystem realities. India’s cyber security framework should be able to adapt and be resilient to protect against intrusions at all levels – in the public sector including critical infrastructure and citizen services, enterprise systems, and public and private data assets.
“A global domain within the information environment consisting of the interdependent network of information technology infrastructures, including the Internet, telecommunications networks, computer systems, and embedded processors and controllers.“
-- A Definition of Cyberspace
Rapid Development in Information Technology
- Speed of Microprocessor chips doubles every 12-18 months
- Storage Density doubles every 12 months
- Bandwidth is doubling every 12 months
- Price keeps dropping making technology affordable & pervasive
- The New “Net” monitors & controls critical Infrastructure. Its integrity & availability is critical for economy, public safety, & national security
Cyber What? Defining Cyber:
Cyberspace is the connected Internet Ecosystem. Trends Exposing critical infrastructure to increased risk:
- Interconnectedness of Sectors
- Proliferation of exposure points
- Concentration of Assets
Cyber Intrusions and Attacks have increased dramatically over the last decade, exposing sensitive personal and business information, disrupting critical operations, and imposing high costs on the economy. Cyber Security is protecting our cyber space (critical infrastructure) from attack, damage, misuse and economic espionage.


Disclaimer: Copyright infringement not intended.
Need For Cybersecurity:
- Government’s digital push: Various programs of government such as Aadhaar, MyGov, Government e-Market, DigiLocker, Bharat Net etc. are prompting a larger number of citizens, companies and government agencies to transact online.
- Start-ups digital push
- India the fifth most vulnerable country in the world in terms of cybersecurity breaches.
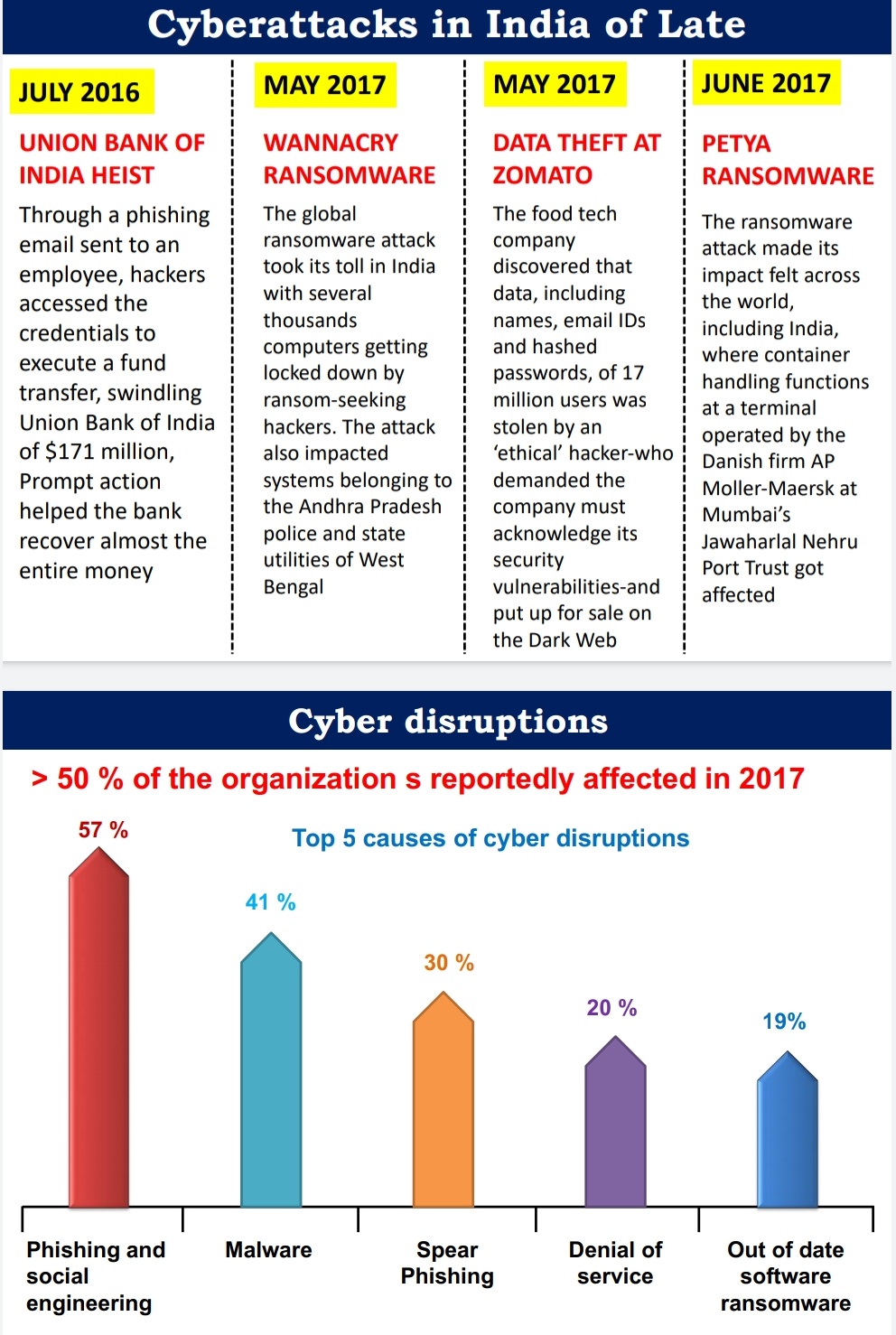
- India saw at least one cybercrime every 10 minutes during the first half of 2017 including more sophisticated cyber threats such as the WannaCry and Petya ransomware.
- India accounted for 5.09 per cent of all cyberattacks such as malware, spam and phishing attacks detected globally in 2017.
- The estimated cost of cyber-attacks in India stands at four billion dollars which is expected to reach $20 billion in the next 10 years.
- India ranks 3rd in terms of number of internet users after USA and China. By 2020, India is expected to have 730 million internet users with 75% of new users from rural areas. The number has grown 6-fold between 2012-2017 with a compound annual growth rate of 44%.
- India secures a spot amongst the top 10 spam-sending countries in the world alongside USA
- India was ranked among the top five countries to be affected by cybercrime, according to a 22 October report by online security firm ”Symantec Corp”.
Recent Breach Incidents:
The Indian Computer Emergency Response Team (CERT-In) has reported a rapid increase in the number of cyber security incidents in recent years: a steep four-fold rise of incidents from 53,117 in 2017 to 208,456 in 2018. For 2019, between January and May, there were 105,8496 such incidents (phishing, network scanning and probing, virus / malicious code and website hacking).
Disclaimer: Copyright infringement not intended.
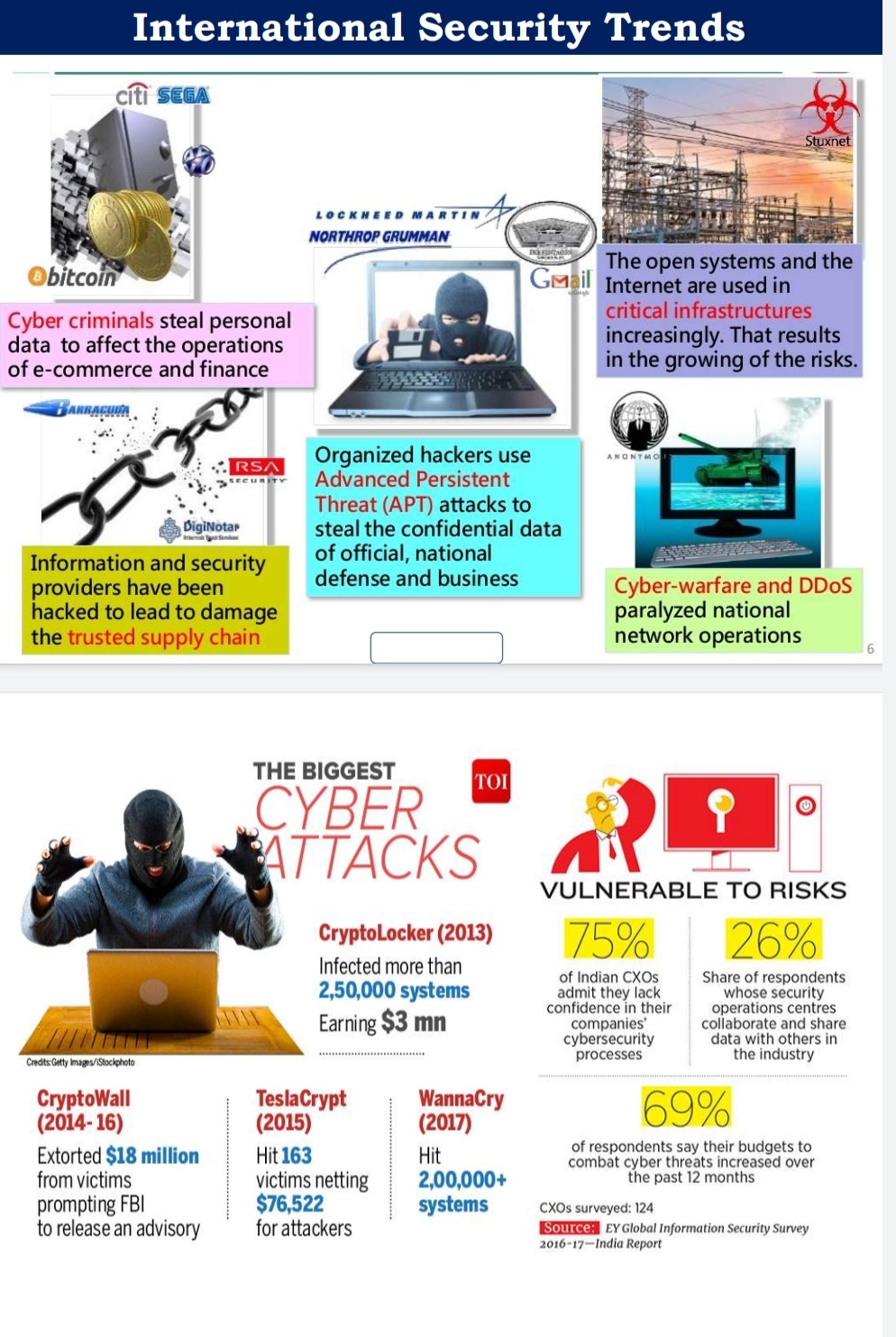
- The WannaCry and NotPetya incidents showed that attacks targeting the digital elements of utility infrastructure such as power plants, services such as banks or hospitals servers, and devices including mobiles and personal computers, have damaged critical national assets.
- In March 2017, hackers took advantage of a bug in the Unified Payment Interface (UPI), leading to losses of around INR 250 million for Bank of Maharashtra customers. Other threats to digital payments include malware installations, phishing attacks, SIM card swap attacks and unreliable devices and infrastructure.
- From the Cambridge Analytica data-mining scandal that affected millions of citizens worldwide, to foreign efforts to manipulate elections and fears of spying on crucial communications networks, we have been reminded time and again that cyber security threats carry across borders.
- The recent revelations from WhatsApp on a targeted Pegasus spyware intrusion by Israel based NSO Group that led to a yet to be ascertained number of journalists, academics and activists being surveilled upon via their mobile devices (including private data such as passwords, contact lists and text messages). This highlights the pernicious tools that can affect individual citizens even as NSO Group has claimed that it only licenses products to vetted State agencies across the globe.
- Recently, there were cyber-attacks on Kudankulam Nuclear Power Project (KKNPP). This has again highlighted the vulnerabilities of our cybersecurity infrastructure.
Disclaimer: Copyright infringement not intended.
Challenges in Ensuring Cyber Security:
- Widespread digital illiteracy
- Use of Substandard devices
- Rampant use of unlicensed software and underpaid licenses also make them vulnerable.
- Lack of adoption of new technology
- Lack of uniform standards
- Import dependence
- Lack of adequate infrastructure and trained staff
- Anonymity
- Lack of coordination among various agencies working for cyber security
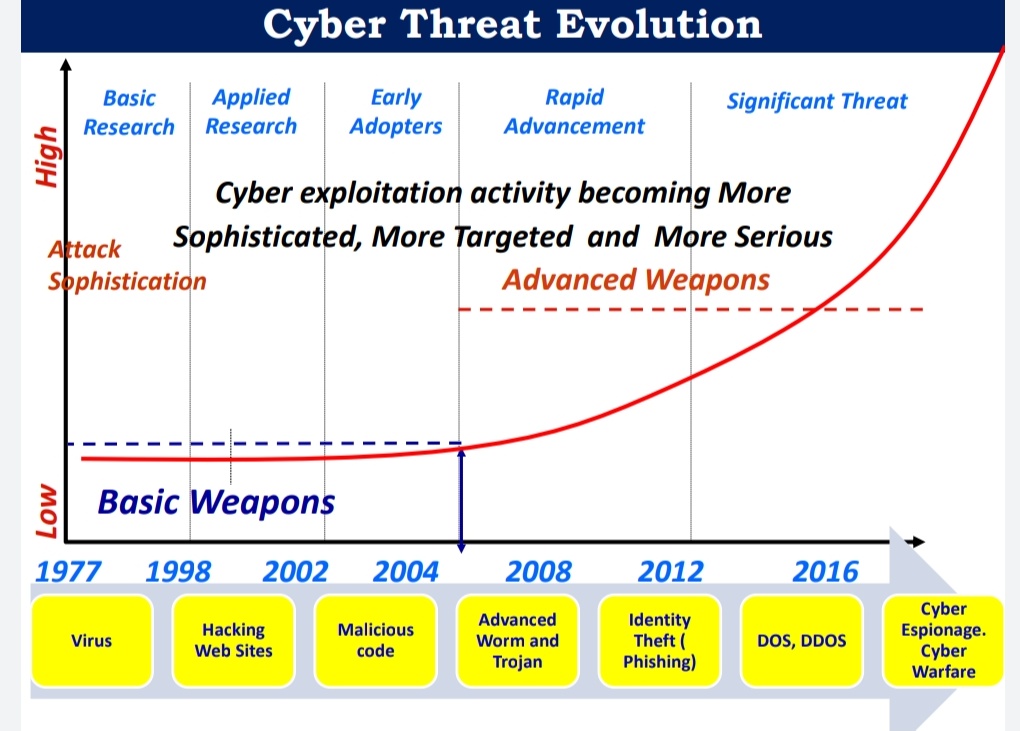
Cyber Threats and Sources:
Sources
- a) Nation States
- b) Cyber Criminal Organisations
- c) Terrorists, DTOs, etc.,
- d) Hackers / Hacktivists
Threats
- Malware – Malicious software to disrupt computers
- Viruses, worms
- Theft of Intellectual Property or Data
- Hactivism – Cyber protests that are socially or politically motivated
- Mobile Devices and applications and their associated Cyber Attacks
- Social Engineering – Entice Users to click on malicious links
- Spear Phishing – Deceptive Communications (e-mails, texts, tweets)
- Domain Name System (DNS) Attacks
- Router Security – Border Gateway Protocol (BGP) Hijacking
- Denial of Service (DoS) – blocking access to websites
Disclaimer: Copyright infringement not intended.
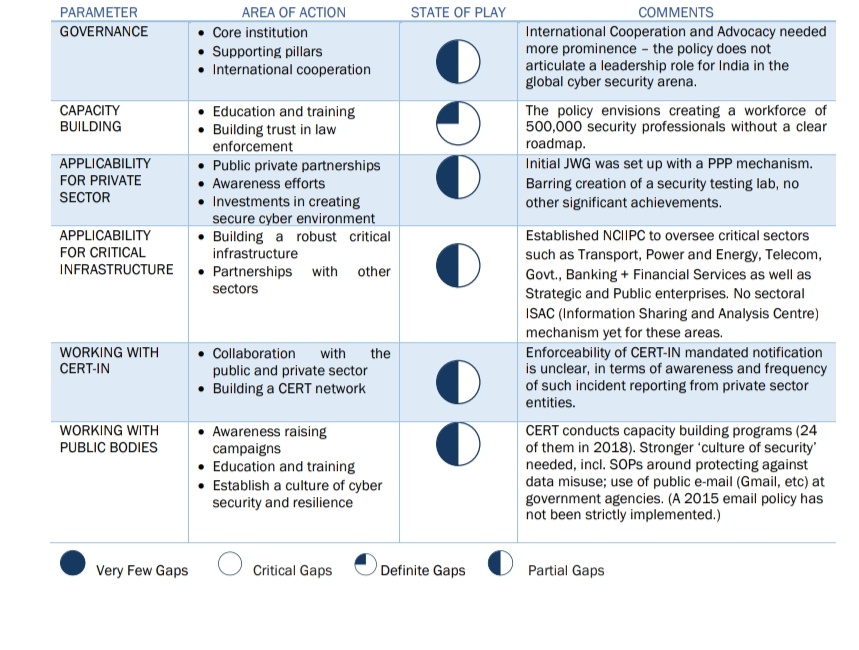
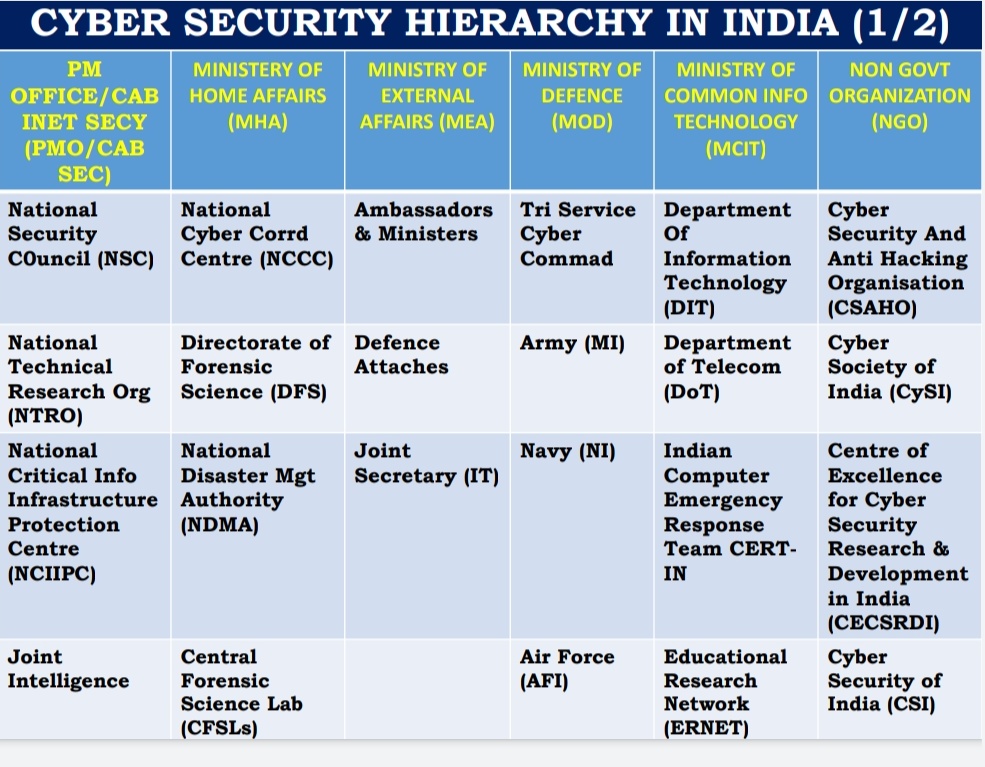
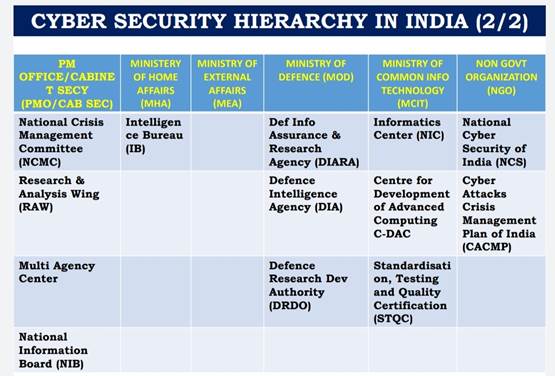
Institutional Framework:
THE INFORMATION TECHNOLOGY ACT 2000 continues to be the omnibus legislation that governs cyber security policy in the country, and it includes provisions for digital signatures, e-governance, e-commerce, data protection, cyber offences, critical information infrastructure, interception and monitoring, blocking of websites and cyber terrorism. Rules under the Act are issued from time to time.
In addition to this legislation, regulatory guidelines are issued by sectoral regulators such as the banking regulator Reserve Bank of India (RBI), telecom regulator Telecom Regulatory Authority of India (TRAI), capital markets regulator Securities and Exchange Board of India (SEBI), and insurance regulator Insurance Regulatory and Development Authority (IRDA), for organizations under their purview.
INDIAN COMPUTER EMERGENCY RESPONSE TEAM (CERT-IN), established within the Ministry of Electronics and Information Technology (MeitY), issues alerts and advisories regarding the latest cyber threats and countermeasures on a regular basis, and has published guidelines for securing IT infrastructure.
The NATIONAL CYBER SECURITY POLICY (NCSP) 2013 document was prepared by the Ministry of Communications and Information Technology to facilitate the creation of a secure cyberspace ecosystem and strengthen the existing regulatory frameworks. The mission was to protect information infrastructure systems, build capacities for preventive and response functions to rising cyber threats, and mitigate vulnerabilities and damage from cyber incidents through a mixture of institutional structures, people, processes, technology and cooperation.
The Office of the NATIONAL CYBER SECURITY COORDINATOR (NCSC) was established under the National Security Council Secretariat as the nodal agency for cyber security established for the purpose. The office coordinates with the central government arms, the states and union territories, and global law enforcement agencies (LEAs) abroad.
The National Cyber Security Policy 2013 policy document is in the nature of a basic framework and provides an initial approach on cyber security from the perspective of protecting data of enterprises and individuals. It referenced protection of strategic digital assets and critical information infrastructure, without significant details of implementation.
Disclaimer: Copyright infringement not intended.
Post the NCSP 2013, numerous initiatives to build a strong national cyber security ecosystem were launched:
- Critical Information Infrastructure Protection: The National Critical Information Infrastructure Protection Center (NCIIPC) was established for the protection of critical information infrastructure in the country, as per the provisions of section 70A of the Information Technology (IT) Act, 2000. It released the first version of its guidelines for protection of critical sectors of the Indian economy in 2013. The second version of was released in 2015. The guidelines specify five levers of control: planning, implementation, operational, disaster recovery/business continuity planning, reporting and accountability.
- Information Technology (The Indian Computer Emergency Response Team and Manner Of Performing Functions and Duties) Rules, 2013 (CERT-In Rules 2013): The Rules outline of proactive measures for protecting cyber security, including forecasts and alerts on security incidents, and the prediction and prevention of future incidents. The guidelines however lack regulatory accountability in terms of treatment and quality of response to security incidents.
- National Information Security Policy: The Ministry of Home Affairs (MHA) developed the National Information Security Policy and related guidelines in August 2014 for securing classified information in all government organizations.
- Draft IoT Policy: This was released (in two versions) by MeiTY in 2014-15 with a view to solicit inputs from the industry and others on cyber security concerns in the IoT ecosystem.
- Draft M2M (Machine-To-Machine) Telecom Roadmap: Developed by DoT and released on May 12, 2015 discusses cyber security issues in M2M interactions.
- SEBI Circular on Cyber Security And Cyber Resilience Of Stock Exchanges: Securities regulator SEBI, as a member of IOSCO10, issued a circular in July 2015 adopting the Principles for Financial Market Infrastructures (PFMIs) laid down by the Committee on Payments and Market Infrastructures (CPMI) at IOSCO. Principle 17 of PFMI requires that systemically important market infrastructures institutions “should identify the plausible sources of operational risk, both internal and external, and mitigate their impact through use of appropriate systems, policies, procedures, and controls. The framework adopts the five functions approach laid down by US-based standard settings organization, National Institute of Standards and Technology (NIST), comprising: Identify, Protect, Detect, Respond and Recover.
- A Draft National Policy On Encryption under Section 84A of the Information Technology Act, 2000 was published on September 21, 2015, and invited comments from the public, but was withdrawn two days later. The draft National Policy on Encryption was withdrawn within two days of its release due to its unfeasible and unclear provisions with respect to the usage of encryption technologies.
- RBI Security Framework for Banking: The Reserve Bank of India in a June 2016 advisory on “Cyber Security Framework in Banks”, had advised banks to improve and maintain customer awareness and education with regard to cyber security risks. Banks were also asked to educate customers on the downside and risk of sharing their login credentials / passwords etc. with any third-party or vendor, and the consequences thereof. Banks were asked to strengthen their cyber security protocols and asked them to report incidents of security breaches. The circular advises banks to evaluate the controls on various aspects including information sharing arrangements with CERT-In, RBI, and the Institute for Development and Research in Banking Technology (IDRBT).
- CERT-In Advisories & Circular on CISOs: CERT-In has advised all banks, Pre-paid Payment Instrument (PPI) issuing agencies and other stakeholders to report cyber security incidents without delay to Indian Computer Emergency Response Team. In March 2017, CERT-In issued guidelines for assigning roles and responsibilities of Chief Information Security Officers (CISOs) in ministries/departments and related agencies managing ICT operations. The core functional aspects of the officers lay in securing applications or infrastructure and compliance.
- Guidelines on Information Security for Insurers: The insurance regulator, Insurance Regulatory and Development Authority of India (IRDAI) issued ‘Guidelines on Information and Cyber Security for insurers’ in March 2017 for providing responsibilities of insurers in ensuring that adequate mechanisms are put in place on issues relating to information and cyber security including requirements related to CISOs.
- Proposed CERT-Fin – The CERT-IN Director General in 2017 led a Working Group that looked at proposed creation of a separate CERT for the financial services sector and invited public comments. The entity is yet to be constituted.
- Creation of Centre Of Excellence For Cyber Security, IB-CART at IDRBT – CERT-IN has created a Centre of Excellence (CoE) for cyber security within IDRBT in Hyderabad. IDRBT works closely with government-owned banks and other public agencies on cyber security related research and issues. The IB-CART, established within IDRBT, is intended to be a common platform for sharing breach information amongst banking entities, on the lines of the FS-ISAC in the US and elsewhere.
- National Digital Communications Policy 2018: In tune with the advancements in the digital communications ecosystem, the National Telecom Policy has now been rechristened as the ‘National Digital Communications Policy’ (NDCP) wherein the Telecom Commission has been now re-designated as the Digital Communications Commission. The central strategic objectives of the policy is to achieve by 2022 (a) broadband for all and (b) propel India to top 50 countries on the International Telecommunication Union (ITU) ICT Development Index. On the three missions to achieve these objectives, ‘Secure India’ outlines a focus on ensuring individual autonomy and choice, data ownership, privacy and security; while recognizing data as a crucial economic resource.
- Ministry of Finance Report on Fintech: In September 2019, a Ministry of Finance committee submitted its final report on fintech related issues. The Committee report also looks at fintech for cyber security and fraud control. The report recommends that fintech firms specializing in this field should be encouraged to set up their businesses in India and provided necessary regulatory approvals for expanding their services in the country.
- Creation of Power-Sector CERTs – Four power sector CERTs have been created to oversee power generation, transmission and distribution parts of the electricity value chain. This is the only sector, with a developed eco-system of functioning CERTs for sharing breach information.
- Creation of ReBIT within RBI – The central bank RBI created ReBIT as its IT subsidiary in 2018, focused primarily on the issue of data and cyber security across the institution and to advise it on cyber-risks in the banking sector.
- CERT-In Training and Capacity Building with Government Agencies - CERT-IN conducts regular training programs for network / system administrators and Chief Information Security Officers (CISOs) of government and critical sector organizations regarding securing IT infrastructure and mitigating cyberattacks. (24 such training programs were conducted in 2018). Cyber security mock drills and exercises are being conducted regularly to enable assessment of cyber security posture and preparedness of organizations in government and critical sectors. 43 exercises have so far been conducted by CERT-In where organizations from different sectors such as Finance, Defence, Power, Telecom, Transport, Energy, Space, IT participated.
- National Cyber Coordination Centre (NCCC) - was set up to generate necessary situational awareness of existing and potential cyber security threats and enable timely information sharing for proactive, preventive and protective actions by individual entities. Phase-I of NCCC has been made operational.
- MeitY Initiatives - 84 security auditing agencies have been empaneled to support and audit implementation of Information Security Best Practices. The government has launched the ‘Cyber Swachhta Kendra’ (Botnet Cleaning and Malware Analysis Centre) that provides detection of malicious programs and free tools to remove them. MeitY has also set up a Cyber Lab at National Law School of India University (NLSIU) Bangalore for creating cyber-crime awareness and cyber forensic training.
- Cyber Crime Awareness Amongst Law Enforcement Agencies (LEAs) – MeitY has engaged with the Data Security Council of India (DSCI) for creating cybercrime awareness among law enforcement authorities through workshops at different cities across India. For security awareness and capacity building, MeiTY has also set up Cyber Forensics Training Labs at policy headquarters in (i) all north-eastern states in collaboration with CDAC11, (ii) cities of Mumbai, Pune, Bangalore and Kolkata, with the help of DSCI for creating Cyber Crime Awareness and Cyber Forensics Training for both LEAs and judiciary (included judges, judicial officers and public prosecutors).
Disclaimer: Copyright infringement not intended.
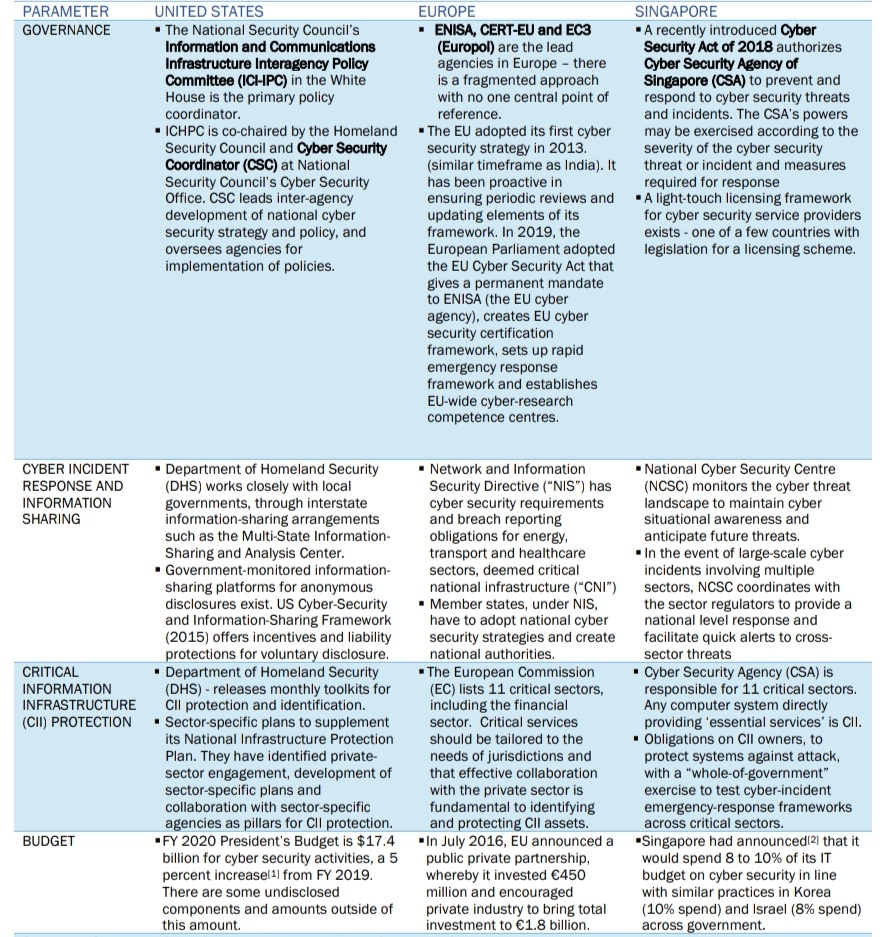
Global Cyber Security Norms and Frameworks:
The OECD’s report, ‘Cyber Security Policy-Making at a Turning Point’13 reveals that cyber security strategies developed by different nations share some common elements. Shared approaches include four elements:
- States’ need for enhanced internal operational coordination;
- Reliance on private-public partnerships,
- Interest in improved international coordination,
- The need to protect fundamental values in cyberspace.
- There have been multiple global forums such as Global Commission on the Stability of Cyberspace (GCSC).
- ITU Global Cyber Security Agenda & Global Cyber Security Index (GCI): identifies five strategic pillars: legal, technical, organizational, capacity-building, and cooperation15. The Global Cyber Security Index (GCI) is a product that emerges from the ITU Plenipotentiary Resolution 130 on strengthening the role of ITU in building confidence and security in the use of information and communication technologies. The goal is to foster a global culture of cyber security and its integration at the core of information and communication technologies. The first GCI survey was conducted in 2014. A big reason for India’s slipping from rank 5 to 47 in four years in the ITU Global Cyber Security Index in 2018 was its weak collaborations between public agencies, and between government and industry.
- Tallinn Manual 2.0 - The Tallinn Manual 2.0 on the International Law Applicable to Cyber Operations16, authored by 19 international law experts, is updated and considerably expanded second edition that was unveiled in 2017. It is an influential resource for legal frameworks around cyber issues developed at NATO’s Cooperative Cyber Defence Centre of Excellence. The manual details four sections comprising general legal principles in the cyber domain as well as specific specialized legal regimes.
- UN Group of Governmental Experts (UN GGE) - The UN GGE on developments in the Field of Information and Telecommunications in the Context of International Security comprises 20 nations equitably distributed based on geography and includes nation states regarded as leaders in cyber areas. The UN GGE released a consensus report in 2015 which proposes norms of responsible behaviour and includes commentary on applicable principles of international law in the cyberspace. A final consensus could not be reached due to its rejection by a few states including Cuba and, reportedly, Russia and China.
- The UN General Assembly adopted two resolutions on cyber, one creating a working group to study cyber norms and possible dialogues, and another setting up a working group of government experts to study applicability of international law to states in cyberspace. UN Secretary General Guterres created a High-level Panel on Digital Cooperation bringing together public and private sector stakeholders.
- Paris Call for Trust And Security In Cyberspace – This was launched by French President Emmanuel Macron in November 2018, as a high-level declaration for cooperation endorsed by 64 countries, international NGOs, universities and hundreds of private companies.
- Open Ended Working Group (OEWG) At UN - The UN General Assembly established an Open-Ended Working Group (OEWG) on informational security that convened for the first time in 2019 around consultative meetings with industry, NGOs and academia on developing norms of responsible State behaviour in cyber space.
- Cyber security Tech Accord: Around 34 global technology and security companies came together in the 2018 RSA Conference to sign a Cyber security Tech Accord to advance online security and resilience around the world. The signatories of the Tech Accord pledge to “protect and empower civilians online and to improve the security, stability and resilience of cyberspace.”
- Budapest convention on cybercrime: This convention of the council of Europe is the only binding international instrument on this issue that addresses Internet and computer crime by harmonizing national laws, improving legal authorities for investigative techniques, and increasing cooperation among nations.
Disclaimer: Copyright infringement not intended.
Trends, Challenges and Threats:
- AI and machine learning can boost cyber defenses
- Ransomware has been a growing threat for the last few years, but it continues to claim high profile victims.
- There is a need of handling data breaches gracefully: It may prove impossible to eradicate data breaches completely, but every organization has the power to lessen the blow by handling the aftermath correctly.
- The IoT is a weak link: We’re rolling out more and more sensor-packed, internet-connected devices, but the Internet of Things remains a major weak point for defenses. All too often these devices lack basic security features, or they aren’t properly configured and rely upon default passwords that can give attackers easy access.
- There’s still a skills shortage
- Developing a common language is the need of the hour: As more organizations and cybersecurity experts come together to develop a common language, our collective defenses grow stronger.
- 5G wireless networks will connect over 7 trillion wireless devices serving over 7 billion people, ushering a new era of security threats, which could arise in following forms:
- Decentralized security needs
- Critical infrastructure protection
- Network Switching: When a 5G device switches to 3G or 4G, it is exposed to the vulnerabilities that haven’t been addressed in the previous generations’ protocol.
- Secure Cloud Computing
- More bandwidth will strain current security monitoring
Way Forward:
- Ensure coordination
- Cyber deterrence
- Establishing cyber insurance framework
- Promote investment in cybersecurity by businesses
- Amendment of IT Act 2008: The regulations need to keep pace with the changing cyber scenario to ensure penalties serves as deterrence for crimes.
- Skill development
- Updation of cyber security policy.
- Regular Security audit
- Establishing cybersecurity framework at state level
- Enhanced international cooperation
https://timesofindia.indiatimes.com/india/70-indian-government-private-websites-face-international-cyber-attacks-over-prophet-row/articleshow/92167143.cms
1.png)













