Free Courses Sale ends Soon, Get It Now


Free Courses Sale ends Soon, Get It Now



Disclaimer: Copyright infringement not intended.
Context
About the Delhi Declaration on Cybersecurity
With the adoption of the declaration, G-20 countries would commit to the following:
Need for agreement on Cybersecurity
International Agreements and initiatives
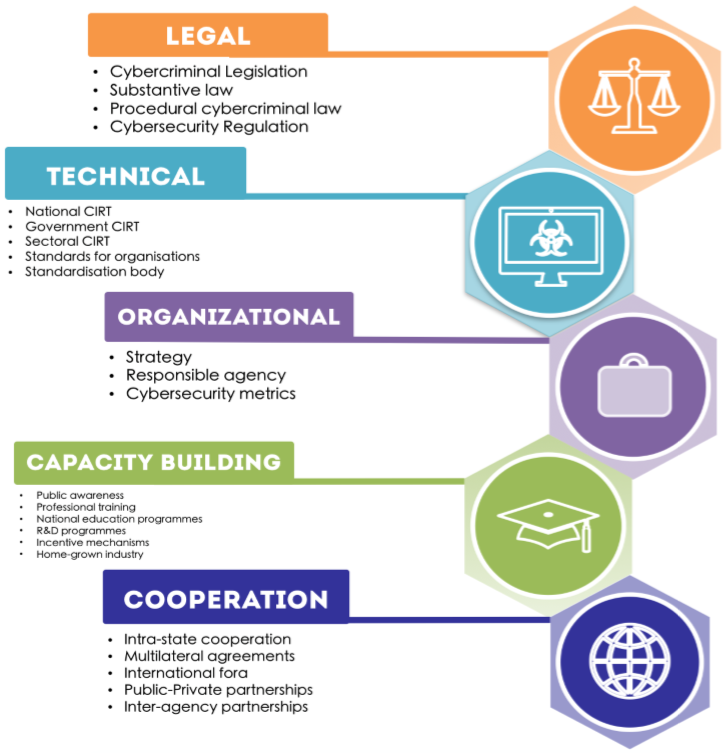
Image: Pillars of the Global Cybersecurity Index, Disclaimer: No copyright infringement is intended.
Way ahead
Conclusion
It is the need of the hour to frame a comprehensive and effective national cybersecurity strategy and international framework with respect for sovereignty of countries and with effective participation of all stakeholders. The Delhi declaration on cybersecurity is thus a step towards the right direction.
|
PRACTICE QUESTION Q) Consider the following statement about the Budapest Convention on Cyber security: 1. It is the first international treaty seeking to address Internet and computer crime (cybercrime) by harmonising national laws. 2. It was adopted by the UN General Assembly in 2015. 3. India is a signatory of the convention. How many of the above statements is/are correct?
Ans: A |
https://epaper.thehindu.com/ccidist-ws/th/th_delhi/issues/38621/OPS/G05BAOEM8.1+GV2BAP8AC.1.html
https://www.intgovforum.org/en/filedepot_download/8395/1896
© 2024 iasgyan. All right reserved