Copyright infringement not intended
Picture Courtesy: terranovasecurity.com
Context: The Indian government has issued a warning about a new scam known as 'Smishing,' a combination of SMS and phishing. It employs deceptive wording to fool users into disclosing sensitive information. Smishing has developed as a big issue as people's dependency on mobile phones grows, necessitating users to remain attentive and aware.
Details
- The government announced that if someone falls prey to Smishing by mistake, they can call 1930 to report online financial fraud and report any cybercrime at cybercrime.gov.in. However, prevention is better than cure, so it is advisable to avoid clicking on suspicious links or sharing personal information over text messages, especially if they are unsolicited.
Smishing
Meaning
- Smishing is a term that combines the words "SMS" and "phishing." It is a type of cyber attack that uses text messages to trick people into giving away sensitive information, such as passwords, credit card numbers, or personal identification details.
- Smishing attackers often pretend to be legitimate organizations or individuals and use urgent or threatening language to pressure their targets into responding. Smishing can lead to identity theft, financial losses, or malware infections.
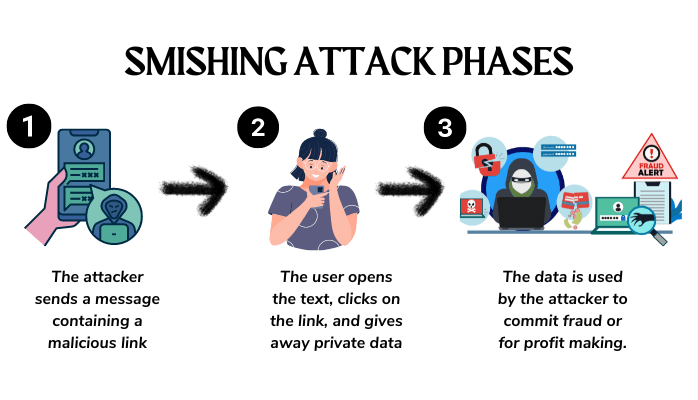
How It Works
Initial Contact
- Attackers often obtain phone numbers from various sources, such as data breaches or public directories. They then send out text messages to these potential victims, disguising themselves as reputable institutions or well-known companies. By posing as legitimate entities, they increase the likelihood of recipients trusting the messages.
Urgent or Alarming Content
- The content of the smishing message is carefully crafted to trigger a sense of urgency or alarm in the recipient. This urgency prompts the recipient to take immediate action without thoroughly thinking through the situation. The messages might claim that there's been suspicious activity on their account, a pending transaction that requires verification, or a security breach that necessitates immediate attention.
Deceptive Links
- The text messages typically include links that direct recipients to fraudulent websites. These websites are designed to look nearly identical to the legitimate websites of the organizations being impersonated. The attackers go to great lengths to mimic the design, logos, and overall appearance of the real websites to make them appear genuine.
Data Collection
- When victims click on the provided links, they are taken to these fake websites, where they are prompted to input their sensitive information. This could include usernames, passwords, credit card numbers, social security numbers, and other personal details. Once victims enter this information, the attackers harvest it. This stolen data can then be used for various malicious purposes, such as unauthorized access to accounts, financial fraud, or identity theft.
Impact
Financial Loss
- Once attackers have access to victims' financial information, they can carry out unauthorized transactions that lead to direct financial losses. Stolen credit card numbers or banking credentials can be used to make purchases or transfers without the victim's consent.
Identity Theft
- Stolen personal information can enable attackers to commit identity theft. This can involve opening new lines of credit, applying for loans, or conducting other fraudulent activities in the victim's name. Recovering from identity theft can be a complex and time-consuming process, with potential long-term consequences for credit scores and financial stability.
Privacy Violation
- Personal information gathered from smishing attacks can be misused in various harmful ways. For instance, attackers might engage in blackmail, using the stolen data to extort money or coerce victims into certain actions. Additionally, the attackers might engage in stalking or other forms of harassment using the victim's private information.
Reputation Damage
- If sensitive personal data obtained through a smishing attack becomes public, it can have severe consequences for the victim's reputation. This is particularly problematic if the stolen information is embarrassing, incriminating, or damaging in some way. Reputation damage can impact both personal and professional spheres.
In addition to these impacts, it's important to note that organizations can also suffer from the fallout of smishing attacks. If attackers successfully impersonate a company and gather sensitive customer information, it can lead to loss of customer trust, legal liabilities, and damage to the company's brand and reputation.

Steps Taken by India
Awareness Campaigns
- Conducting awareness campaigns is crucial to educating the public about the risks posed by smishing and other cyber threats. By providing information on how smishing attacks work, common tactics used by attackers, and prevention measures, individuals can become better equipped to recognize and avoid falling victim to such attacks. Cybersecurity awareness campaigns often include informative materials, workshops, and public service announcements to reach a wide audience.
Reporting Mechanisms
- Introducing a dedicated phone number like 1930 for reporting online financial fraud and cybercrimes is a significant step toward encouraging victims to report incidents promptly. Having a centralized reporting mechanism makes it easier for individuals to report smishing incidents, as well as other cybercrimes, and helps law enforcement and cybersecurity agencies to take appropriate action against the perpetrators.
Cybercrime Portals
- Cybercrime portals like cybercrime.gov.in play a crucial role in providing individuals with resources and information to report and address cybercrimes, including smishing. These portals typically offer guidance on how to report incidents, steps to take after falling victim to a cybercrime, and information about the legal procedures and resources available for victims.
Challenges
Evolving Tactics
- Cyber attackers are known for their ability to evolve and adapt their tactics in response to security measures and awareness campaigns. This constant evolution means that individuals need to stay informed about the latest smishing techniques and remain vigilant in identifying suspicious messages. This challenge emphasizes the need for continuous education and proactive cybersecurity measures.
Human Vulnerability
- Smishing attacks often exploit human psychology, playing on emotions like fear, curiosity, and urgency. By manipulating these emotions, attackers increase the likelihood of victims responding impulsively without critically evaluating the situation. Overcoming this challenge requires not only cybersecurity education but also an understanding of social engineering tactics and how to recognize them.
Global Nature
- The digital nature of smishing allows attackers to launch their campaigns from anywhere in the world. This geographical anonymity makes it challenging to track down and prosecute perpetrators, as they can hide behind various layers of anonymity, including VPNs and Tor networks. International collaboration between law enforcement agencies becomes essential to address this challenge effectively.
Digital Illiteracy
- Digital literacy disparities can leave certain individuals more vulnerable to smishing attacks. People who are not well-versed in technology and online security may struggle to differentiate between legitimate messages and fraudulent ones. Bridging the digital divide through education and accessible resources is crucial to minimizing this vulnerability.
Way Forward
Continuous Education
- Regular and consistent awareness campaigns are crucial to ensure that individuals are up-to-date with the latest smishing tactics and prevention strategies. By raising awareness, people can be more cautious and better equipped to identify and avoid falling victim to these attacks.
Digital Literacy Programs
- Integrating cybersecurity education into educational institutions and community organizations is a proactive way to empower individuals, particularly the younger generation, with the knowledge and skills needed to navigate the digital landscape safely.
Technological Solutions
- Developing advanced detection mechanisms, such as AI-powered algorithms and machine learning, can help mobile carriers and cybersecurity companies identify and block smishing messages in real-time. This proactive approach can significantly reduce the success rate of these attacks.
Collaboration
- Collaboration is essential to effectively combat smishing on a broader scale. By sharing information, best practices, and threat intelligence, various stakeholders can collectively work towards minimizing the impact of smishing attacks.
Enhanced Legislation
- Strengthening cybercrime laws and regulations can provide law enforcement with the necessary tools to investigate and prosecute smishing perpetrators more effectively. Clear legal frameworks can deter attackers and ensure that justice is served.
User-Focused Security Features
- Mobile operating systems and app developers can contribute by integrating user-focused security features. These features might include warning messages when clicking on suspicious links, displaying alerts for potential smishing attempts, and providing tips for identifying fraudulent messages.

Conclusion
- Addressing the smishing threat requires a comprehensive approach involving awareness, education, technological advancements, legislative support, and collaboration among various stakeholders. As technology evolves, individuals and organizations must remain vigilant and proactive to effectively counter this evolving cyber threat.
Must Read Articles:
AKIRA RANSOMWARE: https://www.iasgyan.in/daily-current-affairs/akira-ransomware
LOCKBIT RANSOMWARE: https://www.iasgyan.in/daily-current-affairs/lockbit-ransomware
|
PRACTICE QUESTION
Q. The term “smishing” is frequently seen in the news. What is the meaning of smishing?
A) A type of cybercrime that uses deceptive text messages to manipulate victims into divulging sensitive personal information
B) A type of cybercrime that uses deceptive emails to manipulate victims into divulging sensitive personal information
C) A type of cybercrime that uses deceptive phone calls to manipulate victims into divulging sensitive personal information
D) A type of cybercrime that uses deceptive social media posts to manipulate victims into divulging sensitive personal information
Answer: A
Explanation: Smishing is a type of cyberattack that uses text messages to trick people into giving away their personal or financial information. The term smishing comes from combining "SMS" and "phishing", as the attackers pretend to be legitimate entities and lure the victims into clicking malicious links or downloading harmful attachments.
|
https://zeenews.india.com/technology/govt-warns-citizens-about-smishing-scam-how-to-protect-against-this-online-threat-2654285.html




