Free Courses Sale ends Soon, Get It Now


Free Courses Sale ends Soon, Get It Now


Disclaimer: Copyright infringement not intended.
Context
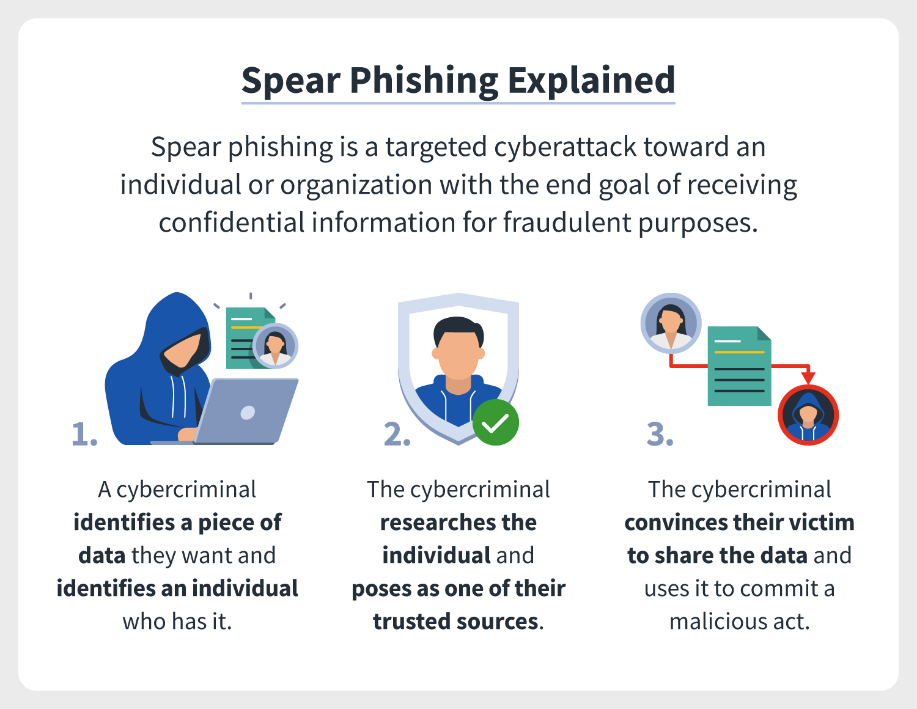
Spear phishing definition
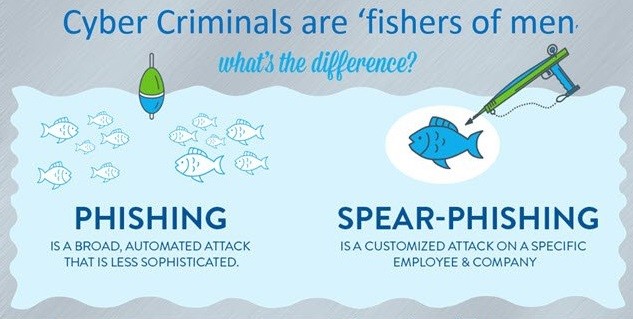
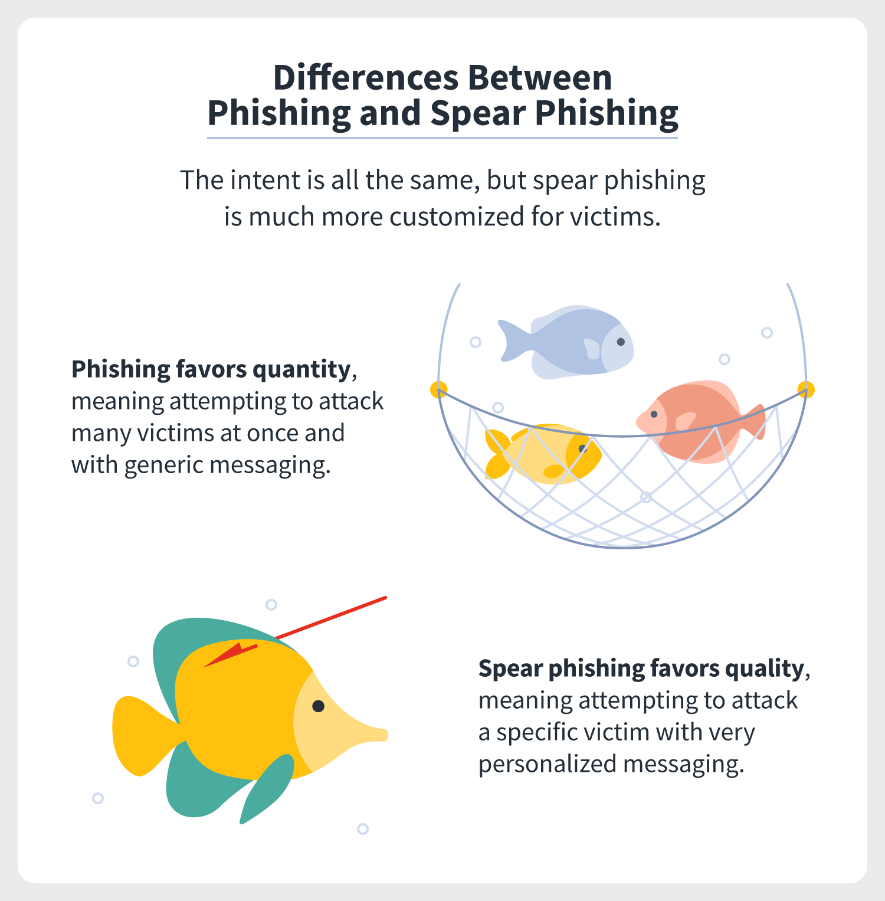
Spear phishing vs phishing
Spear phishing examples
MALWARE AND ITS TYPES: https://www.iasgyan.in/blogs/malwares-and-its-types
|
PRACTICE QUESTION Q. Consider the following statements: 1. A keylogger is a surveillance malware that monitors keystroke patterns. 2. A rootkit is malicious software that enables threat actors to remotely access and control a device. 3. A bot is a self-replicating malware that spreads itself to other devices. 4. Spear phishing is a cybercrime that uses emails to carry out targeted attacks against individuals and businesses. How many of the above statements are incorrect? a. Only one b. Only two c. All four d. None. Answer: d. None. |
© 2024 iasgyan. All right reserved